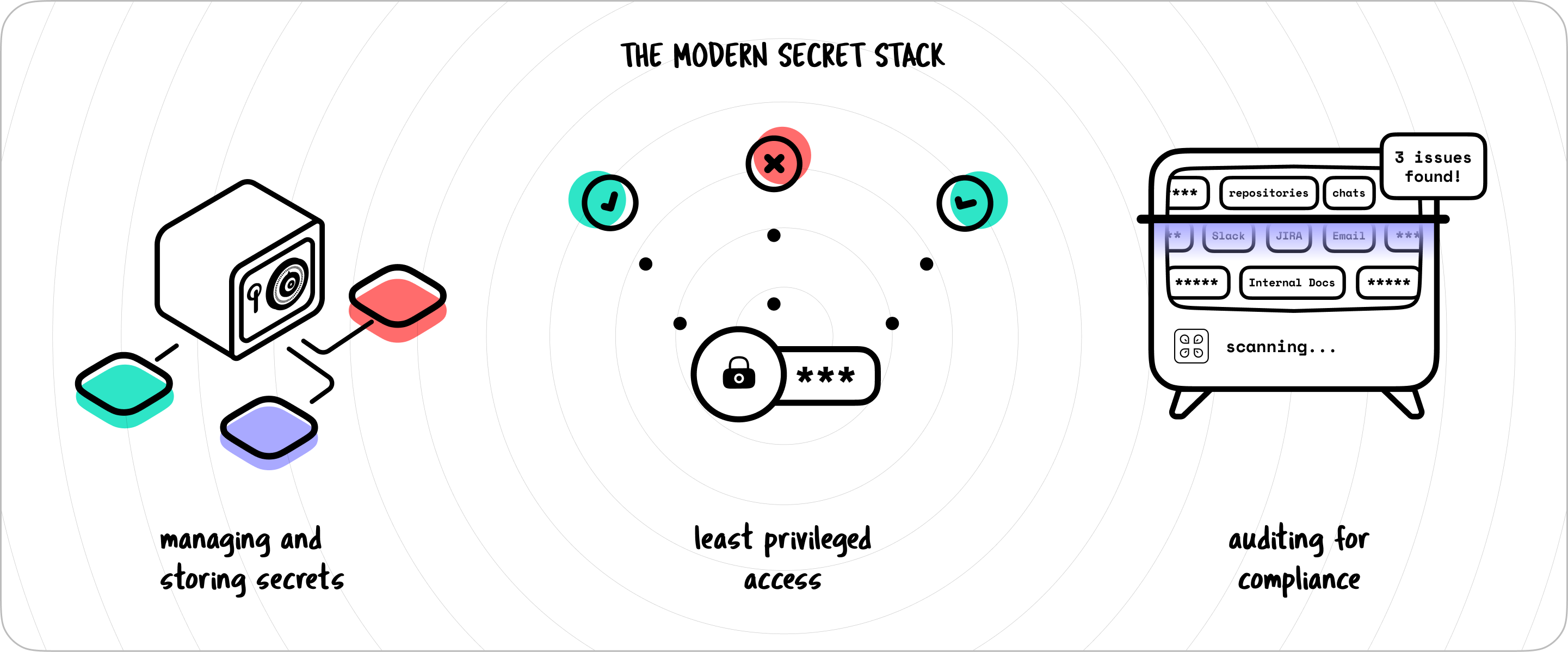
The Modern Secret Stack

If you are a developer, you must have handled secrets in some way.
You’ve probably used a vault for storing them, set up configs to deliver them to different services across different environments, tell other developers to follow a process and raise tickets whenever they want to create or access a secret.
And still, secrets leak, or worse, you don’t know where they are in the first place.

Well, this is happening because you are trying to treat the symptoms individually instead of curing the disease. The evolution of your architecture has far outpaced how you manage your secrets.
You need what we call The Modern Secret Stack.
The Modern Secret Stack
The modern tech architecture is now an interconnected web of microservices, serverless functions, and third-party integrations across multiple points in the stack. Throw in teams working from different corners of the globe, and the picture gets even more rich and multifaceted.
But the way you manage secrets hasn’t evolved with the sophistication of your architecture. The old way of trying to centralize secrets through processes just doesn’t work. It just incentivizes developers to use workarounds to get their work done quickly.
The Modern Secret Stack should give more control over your secrets while allowing developers the freedom that they need.
It should help you:
- Manage secrets without the hassle of setting up endless config files
- Ship secrets without leaks
- Proactively audit for leaks and potential breaches
Manage secrets
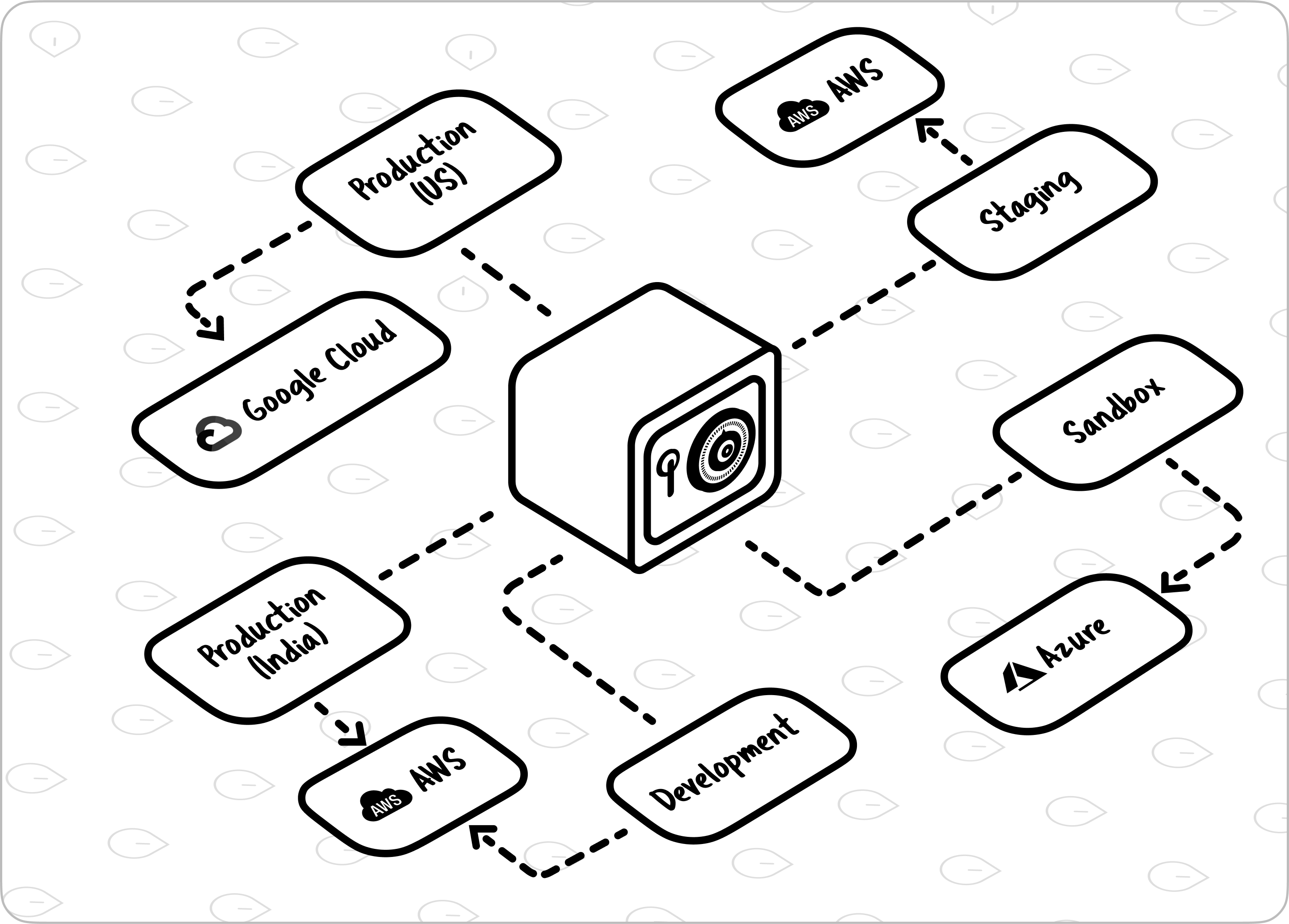
If you are reading this, you probably have a bunch of microservices or lambda functions. You probably would also be integrating with a bunch of API-based SaaS (like Twilio or SES).
Sure, you can ‘store’ secrets in a secret manager, but how do you manage this across different environments? How do you manage this across clouds? What about the RBAC settings for the employee who has left or the new service set up yesterday? And — how do you ensure Dave doesn’t share the secret with Jim on Slack, again?
How do you enable developers to add secrets for a service as quickly as sharing it on Slack? The Modern Secret Stack helps you centralize secret creation and storage without becoming a bottleneck for engineering teams.
Ship secrets without leaks
As a company gets bigger, the number of engineering teams and services goes up. The number of third-party tools that you integrate also goes up. As that happens, different teams start doing things differently.
With secrets, the problem is worse! As the number of engineers grows, so does the number of ways to manage secrets! Some teams may choose to inject secrets during build time, others may choose to use environment variables. Oftentimes, this leads to a user seeing the secret in plaintext while transporting.
Guess what! Once a secret is revealed, it isn’t a secret anymore.
The Modern Secret Stack will transmit the secret to the entity that requested it based on whether it has access or not. It will ensure that you have an airtight secret consumption process with no human access to plain text secrets.
Proactively audit for leaks
You’ve now successfully set up your secrets! But now you need to keep a keen eye on your secrets to see spot potential issues.
Things you built today might not be the same 6 months down, systems drift, and so does your secrets infrastructure.
The Modern Secret Stack should help you:
Control Access Centrally
Viewing who has access to which secrets and audit logs of when each secret was accessed is necessary for security investigations and compliance purposes. This also helps you understand potential risks in the system.
Not just detect leaks, but prevent data-breaches
Secrets often end up in places they shouldn’t be. They sneak into chat apps, hitch a ride on project planning tools, find cozy corners in internal help docs, and sometimes, they even play hide and seek in the code itself!
Your secret stack should help you find leaked secrets.
While it's great to understand leaks, it is even more important to prevent them in the first place.
The Modern Secret Stack should help you detect leaks and prevent breaches by integrating into developer workflows ( CI integrations, pre-commit hooks, etc).
Rotate Secrets at the click of a button
You may need to rotate secrets for two reasons:
- Security and Compliance: A lot of compliance standards require you to rotate secrets periodically to ensure higher standards of security.
- Leaks: Whenever you discover a leaked secret, it must be rotated immediately across all applications and services.
In both cases, rotating secrets is extremely painful and frustrating. You’ll need to coordinate across all teams and hunt for secrets stored in different places (including code) and finally rotate them.
The Modern Secret Management Stack should help you view and rotate secrets from one place ideally at the click of a button.
Ok, But now what?
Since you’ve made it down here, you clearly understand the value of a great secret management service. But you are probably concerned about the engineering bandwidth required to implement all of this 😅
Book a call with our founder to get a state-of-the-art Secret Management Practice up and running for all your services across all environments in less than 10 minutes.

